The correct spelling is HIPAA, which stands for Health Insurance Portability and Accountability Act. The double A makes sense because it reflects the full name of the law. “HIPPA” is a common misspelling based on how the word sounds.
6 Min Read | February 01, 2026
HIPPA or HIPAA? Clearing Common Myths Around HIPAA Compliance Forms
Understanding HIPAA forms starts with spelling it right.
“Hipaa” almost tricks everyone. The word sounds like it should have two ‘p’s’. But it’s actually spelt HIPAA, with an extra A, and not HIPPA, with an extra P.
HIPAA stands for Health Insurance Portability and Accountability Act.
This confusion is very common. People search for hippa form or hippa compliance form without realizing the spelling is off. They trust their ears. They type it fast. The spelling feels correct, while HIPAA stands in the corner and shakes its head.
The spelling mistake is small. HIPAA is not. It is a United States federal law and under HIPAA, healthcare organizations are classified as covered entities. These include clinics, hospitals, wellness centers, telehealth providers, labs, and any group that handles patient information. All covered entities are legally required to protect every piece of patient data they collect. Many of them now rely on digital forms, which makes proper HIPAA compliance more important than ever.
This makes the difference between a casual hippa form and a real HIPAA compliant form very important. A casual form cannot protect Patient Health Information and a covered entity cannot use it. HIPAA has clear rules. Every healthcare organization must follow them to keep patient data safe. The risk is real.
It is important to understand what HIPAA is and why it is required. This article explains HIPAA in simple language. Anyone who collects patient information must follow HIPAA rules.
Here’s what you’ll learn
- HIPAA - What is it and Why the spelling matters
- Who Counts as a Covered Entity and Is Subject to HIPAA Violations
- HIPAA Penalties
- What makes HIPAA forms compliant
HIPAA - What is it and Why the spelling matters
HIPAA is a United States federal law. It was created in 1996 to protect a patient’s personal health information and to make sure healthcare organizations follow proper data security practices. The name stands for Health Insurance Portability and Accountability Act. This is why the correct spelling has two A’s. It is not HIPPA. The spelling reflects the seriousness of the law behind it.
HIPAA sets the rules for how medical information should be collected, stored, used, and shared. It protects everything that can identify a patient. This information is called PHI, or Protected Health Information. PHI includes names, medical history, test results, treatment details, billing records, and anything else linked to a person’s health.
HIPAA applies to groups called covered entities. These include healthcare providers, health plans, and healthcare clearinghouses. It also extends to their business associates, which are vendors or partners that handle patient data for them. All these groups must follow HIPAA rules to keep patient information safe.
HIPAA is made up of several important rules:
- Privacy Rule - This rule controls how PHI can be used and shared. It gives patients rights over their own health information.
- Security Rule - This rule focuses on digital information. It requires safeguards such as encryption, access controls, secure storage, and proper monitoring.
- Breach Notification Rule - This rule requires organizations to notify patients, authorities, and sometimes the media if PHI is exposed or accessed without permission.
Together, these rules ensure that patient information stays private and secure. They also create clear expectations for anyone who collects or handles medical data. HIPAA is not just a set of guidelines. It is a legal requirement. Using the correct spelling helps us talk about it accurately and understand the responsibility it carries.
Who Counts as a Covered Entity and Is Subject to HIPAA Violations
Covered entities under HIPAA are organizations or individuals that handle protected health information (PHI) as part of their work. These groups must follow HIPAA rules at all times. If they fail to protect PHI, they can face civil or criminal penalties. Covered entities fall into three main categories.
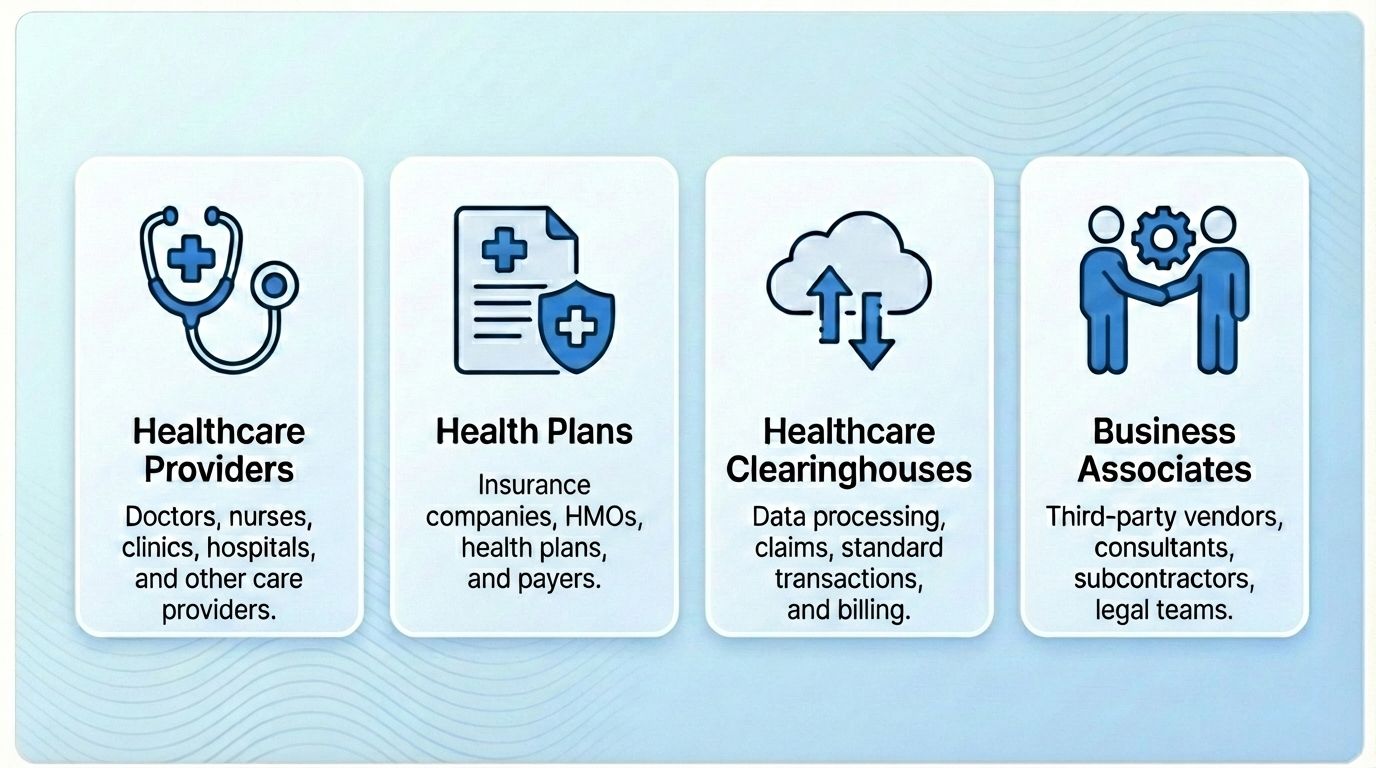
1. Healthcare Providers
A healthcare provider becomes a covered entity when they send health information electronically for any transaction that meets standards set by the Department of Health and Human Services (HHS). This group includes doctors, clinics, hospitals, psychologists, dentists, chiropractors, nursing homes, and pharmacies.
If a provider fails to protect PHI, they can face HIPAA violations through fines, audits, or required corrective actions.
2. Health Plans
Health plans include health insurance companies, HMOs, employer health plans, and government programs such as Medicare, Medicaid, and military or veterans’ healthcare programs.
Health plans must secure all member data. Any improper use, disclosure, or weak safeguard can result in a HIPAA violation.
3. Healthcare Clearinghouses
Healthcare clearinghouses are organizations that take medical data from one system and convert it into a standard format that other systems can read. They also convert standard data back into a non-standard format when needed. This makes it possible for different healthcare systems to communicate with each other.
Common examples include billing services, repricing companies, and community health information systems.
Because clearinghouses receive PHI from many providers and process it on their behalf, they hold large amounts of sensitive data. If they mishandle this information, fail to secure it, or transmit it improperly, they can face HIPAA violations. Their role in routing and converting PHI makes strong compliance essential.
4. Business Associates
Business associates are third party vendors that work with covered entities and handle PHI on their behalf. Examples include online form builders, billing companies, IT vendors, cloud storage services, and analytics tools.
If a business associate mishandles PHI or fails to follow required safeguards, they can also be held liable for HIPAA violations.
HIPAA Penalties - what happens if covered entities don’t follow HIPAA regulations
When HIPAA rules are broken, the law steps in with strict penalties to protect patient data. HIPAA violations fall under two categories. These are civil penalties and criminal penalties.
Each category follows a tiered structure based on negligence, severity, and intent. Penalties can include fines, corrective actions, and even jail time. The law assigns a minimum penalty for each level of negligence, so even small mistakes are taken seriously. The total financial impact can be even higher if multiple violations are found during an investigation.
Civil Penalties
Civil penalties apply when the violation is unintentional or due to reasonable cause.
These fall into four categories:
Category | Description | Penalty |
|---|---|---|
| Category 1 (Unawareness) | The organization did not know about the violation. | $127 to $63,000 per year |
| Category 2 (Reasonable Cause) | Violation due to reasonable cause. Often weak safeguards or accidental disclosure. | $1,000 to $100,000 per year |
| Category 3 (Willful Neglect, Corrective action taken) | Willful neglect occurred but the issue was corrected quickly. | $10,000 to $250,000 per year |
| Category 4 (Willful Neglect, Corrective action not taken) | Willful neglect with no corrective action. | $50,000 to $1.5 million per year |
Criminal Penalties
Criminal penalties apply when PHI is misused intentionally. These penalties increase with intent and harm.
| Tier | Description | Penalty |
|---|---|---|
| Tier 1 (Unauthorized but intentional access or disclosure of PHI | Intentionally viewing or sharing a patient’s information without permission or a valid work reason. | Up to $50,000 and up to 1 year in jail |
| Tier 2 (Obtaining PHI under false pretenses) | Accessing or using patient information with deceptive intent. | Up to $100,000 and up to 5 years in jail |
| Tier 3 (Using PHI for personal gain, financial advantage, or malicious intent) | Individuals knowingly use PHI to deceive or manipulate for their own advantage. | Up to $250,000 and up to 10 years in jail |
Covered entities and their business associates share responsibility for protecting PHI. Any failure to meet HIPAA standards can trigger penalties, regardless of whether the issue was accidental, negligent, or intentional.
What makes HIPAA forms compliant
HIPAA compliance applies to your entire organization, not just your forms. If you are a covered entity or a business associate handling PHI, you must follow HIPAA rules across every system, process, and workflow. HIPAA is built on two major sets of standards called the Security Rule and the Privacy Rule. Together, they define how patient information must be protected.
The Security Rule - The Security Rule focuses on protecting electronic PHI (ePHI). It has three major safeguard categories: technical, administrative, and physical.
1. Technical Safeguards - These protect the technology used to store and transmit ePHI.
- Encryption and decryption: All ePHI must be encrypted during transmission and while stored.
Example: A patient enters their symptoms in an online form. The information travels through a secure HTTPS connection and is stored in an encrypted database. - Access control: Only authorized staff can access PHI.
Example: A nurse can view patient responses. A receptionist can only see appointment details. An intern cannot see any PHI. - Audit controls: Systems must record and track who accesses ePHI.
Example: If a staff member opens a patient response, the system logs their name, the time they viewed it, and the action they took. - Integrity controls: ePHI must not be changed or destroyed without authorization.
Example: A system prevents staff from editing or deleting a patient’s medical notes unless they have the correct role. Any approved change is logged so there is a clear record of what was updated and by whom. - Transmission security: All ePHI must move through secure, protected networks.
Example: When a patient uploads a medical document through a form, the file is sent through an encrypted, secure channel so it cannot be intercepted or read by anyone outside the organization.
2. Administrative Safeguards - These focus on policies, training, and internal management.
- Workforce security: Employees must be trained and given proper access based on their roles.
Example: A new staff member completes HIPAA training before they start work. Their login only allows them to see the PHI needed for their job, not the entire patient database. - Security management: Organizations must conduct regular risk assessments and fix vulnerabilities.
Example: A clinic reviews its systems every year to check for weak passwords, outdated software, or unprotected devices. Any issue found is fixed immediately to prevent a data breach. - Contingency planning: Backup and recovery plans must be in place.
Example: If a server crashes, the clinic can restore all patient records from a secure backup stored in a HIPAA compliant data center. - Security incident procedures: Teams must have a clear process for responding to breaches.
Example: If a staff member accidentally emails PHI to the wrong person, the clinic follows a set protocol that includes reporting the incident, documenting what happened, and notifying affected patients if required. - Business Associate Agreements (BAAs): All third party vendors that handle PHI must sign a BAA.
Example: When a clinic uses an online form builder to collect patient information, the vendor signs a BAA confirming they follow HIPAA rules and will protect all PHI the clinic collects.
3. Physical Safeguards - These protect the places, devices, and hardware where ePHI is stored.
- Data residency: PHI for U.S. patients must be stored in compliant data centers that meet HIPAA’s physical standards.
Example: A clinic uses a HIPAA compliant cloud provider that stores all patient records in secure U.S. data centers with controlled access, surveillance, and proper physical protections. - Facility access controls: Only authorized people can enter areas where ePHI is stored.
Example: A server room with patient data is locked and can only be opened with an access badge. Only IT staff with permission can enter. - Workstation security: Computers that access ePHI must be secured and monitored.
Example: A nurse’s computer automatically locks when not in use. She must log in with a password or badge before viewing patient records. - Device and media controls: Hard drives, USBs, tablets, and other devices storing PHI must be managed, protected, and disposed of safely.
Example: When an old laptop is replaced, the clinic wipes and destroys the hard drive so no patient information can be recovered.
The Privacy Rule
The Privacy Rule defines when and how PHI can be used or shared. This is where consent and patient rights become important.
- Patient authorization: Written consent is required before using PHI for marketing, research, or any non-treatment purpose.
Example: A clinic wants to send marketing emails about a new therapy. They first ask patients to sign a form giving permission to use their PHI for that purpose. - Notice of Privacy Practices (NPP): Patients must be told clearly how their information will be used and shared.
Example: During check-in, a patient receives a document that explains how the clinic stores their records, who can access them, and how their data may be shared for treatment or billing. - Right to access and amend: Patients can view their records and request corrections.
Example: A patient notices an incorrect allergy entry in their medical file. They request a correction, and the clinic updates the record after verifying the information. - Minimum necessary rule: Only share the smallest amount of PHI needed for any task.
Example: When a clinic verifies insurance coverage, it shares only the patient’s name and policy number, not their medical history. - Revocation of consent: Patients can withdraw their consent at any time.
Example: A patient who previously agreed to share their records for a research study later changes their mind. They notify the clinic, and the clinic stops using their PHI for the study from that point onward.
How Does This Apply to Your Forms?
When you collect patient information through online forms, every part of HIPAA applies. Your form builder must use encryption, proper access controls, audit logs, secure hosting, and a signed BAA. It must also follow Privacy Rule requirements for consent, data use, and patient rights.
The form is only one piece of HIPAA compliance, but it is often the first point where PHI enters your system. That is why building HIPAA compliant forms is essential.
MakeForms is HIPAA Compliant
MakeForms is fully HIPAA compliant, and everything mentioned in this HIPAA guide applies directly to our platform. You get all the required safeguards built in, so every form you create meets HIPAA standards from the moment you publish it.
HIPAA compliant features built into MakeForms:
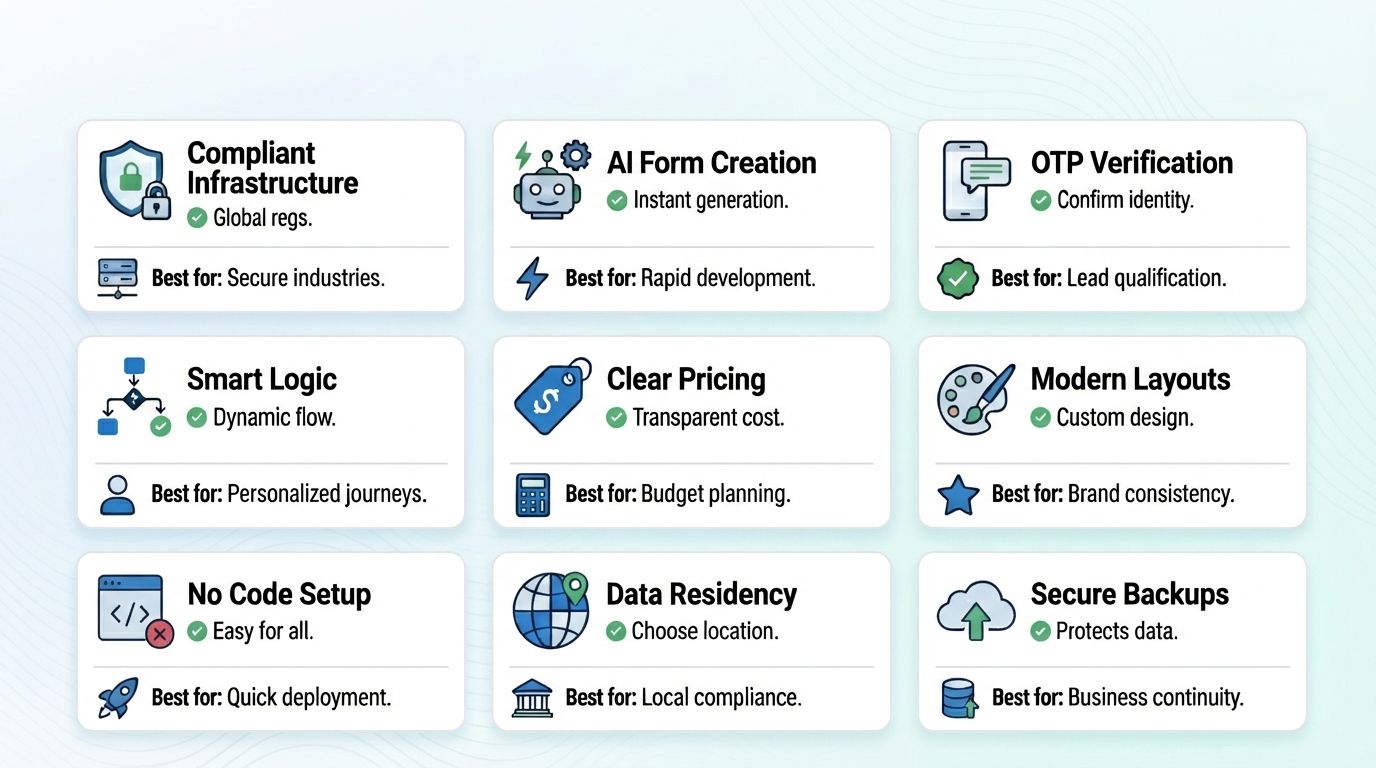
- Fully compliant infrastructure - MakeForms handles encryption, secure hosting, access controls, and a signed BAA. Every form follows HIPAA standards in the background.
- AI form creation - You can create a complete form with a simple prompt. You tell the system what you need. The AI builds the form for you in seconds.
- OTP verification - Forms support email and SMS verification. This keeps out spam and unknown users. It also improves data quality.
- Smart conditional logic - Your form can adjust based on each answer. This creates a smooth and simple experience for users.
- Clear pricing - MakeForms offers simple and affordable plans. You do not pay extra for more responses.
- Modern and branded layouts - Your forms look clean and professional. They match your brand and feel easy to complete.
- No code setup - Anyone on your team can build and launch a HIPAA compliant form. No technical skills are required.
- Data residency controls - Your PHI is stored in the United States in regions that meet HIPAA’s legal and physical requirements.
- Secure backups - All PHI is backed up in restricted-access, monitored data centers to keep your information safe and recoverable at any time.
MakeForms gives you a safe way to collect patient information and keeps your forms aligned with HIPAA rules.
Create a HIPAA Compliant Form in 3 Simple Steps with MakeForms
Creating a HIPAA compliant form on MakeForms is easy, even if you have never built a form before. The platform handles the technical work in the background, so you only focus on what you want the form to do.
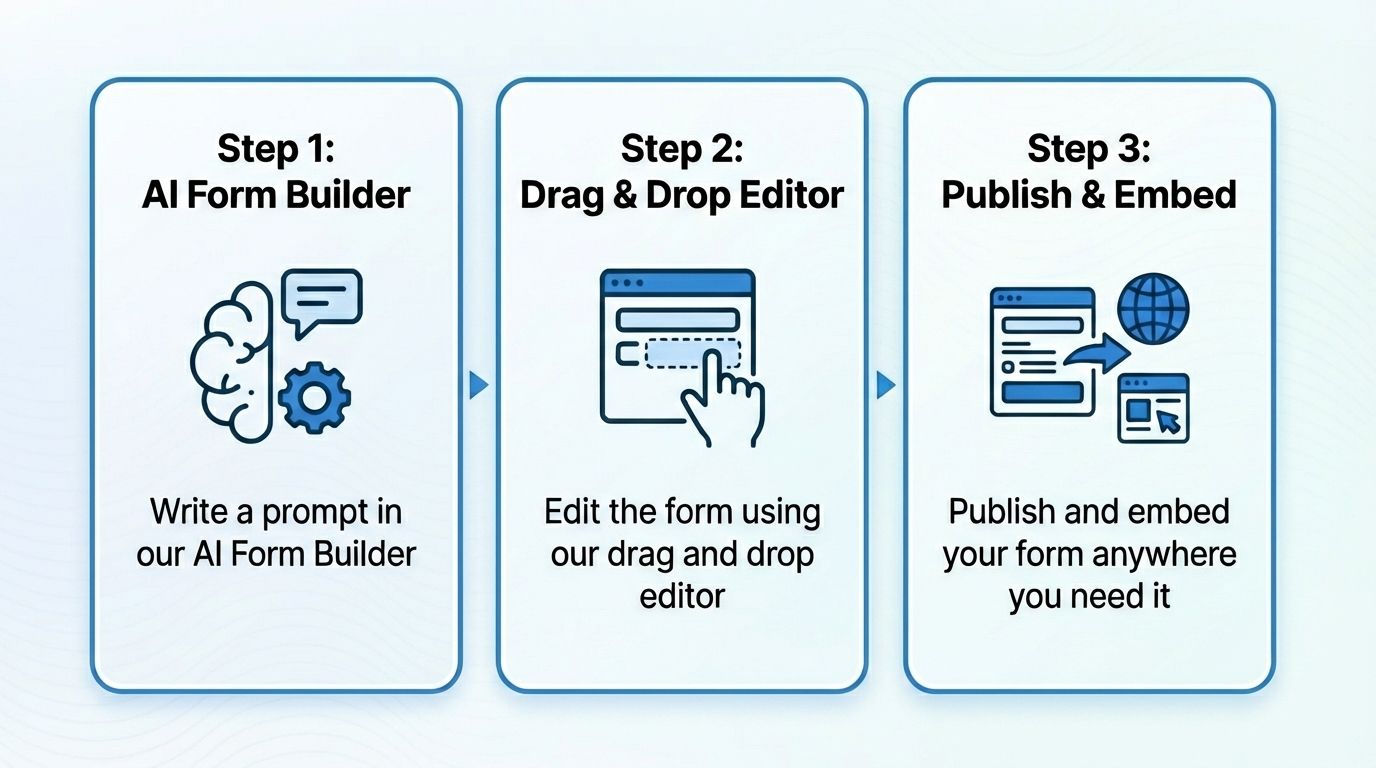
Step 1: Write a prompt in our AI Form Builder
You start by typing what you need. For example, “Create a patient intake form for a dermatology clinic.” The AI instantly generates a complete form with the right questions, structure, and layout.
Step 2: Edit the form using our drag and drop editor
Once the AI builds your form, you can customize it. You can add or remove fields, change the order of questions, add conditional logic, or adjust the design. Everything works through simple drag and drop controls, so you do not need any technical skills.
Step 3: Publish and embed your form anywhere you need it
After editing, you click publish. You can embed the form on your website, share it as a link, or place it inside your patient portal. Every submission is protected under HIPAA, and you can manage responses from your dashboard.
MakeForms keeps every form compliant from the moment you create it. You get a fast, secure, and beginner-friendly way to collect patient information without worrying about the technical details.
Create your HIPAA compliant forms with MakeForms AI - Start your free trial today!

