If your website collects, stores, or transmits any PHI — through forms, chat widgets, analytics, or backend logs — then yes, the entire website must meet HIPAA requirements, not just the form pages.
6 Min Read | January 20, 2026
All healthcare websites collect PHI, here’s how you can protect yourself from HIPAA penalties.
If you’re a healthcare provider, clinic, lab, telehealth brand, or any covered entity handling PHI — you’re required to be HIPAA compliant as an entire organization, not just at the form level.
HIPAA, the Health Insurance Portability and Accountability Act, is a U.S. federal law that protects the privacy and security of patients’ health information. In practice, it sets strict rules for how healthcare organizations collect, store, transmit, and process PHI (Protected Health Information).
So let’s first break down what counts as PHI on your healthcare website.
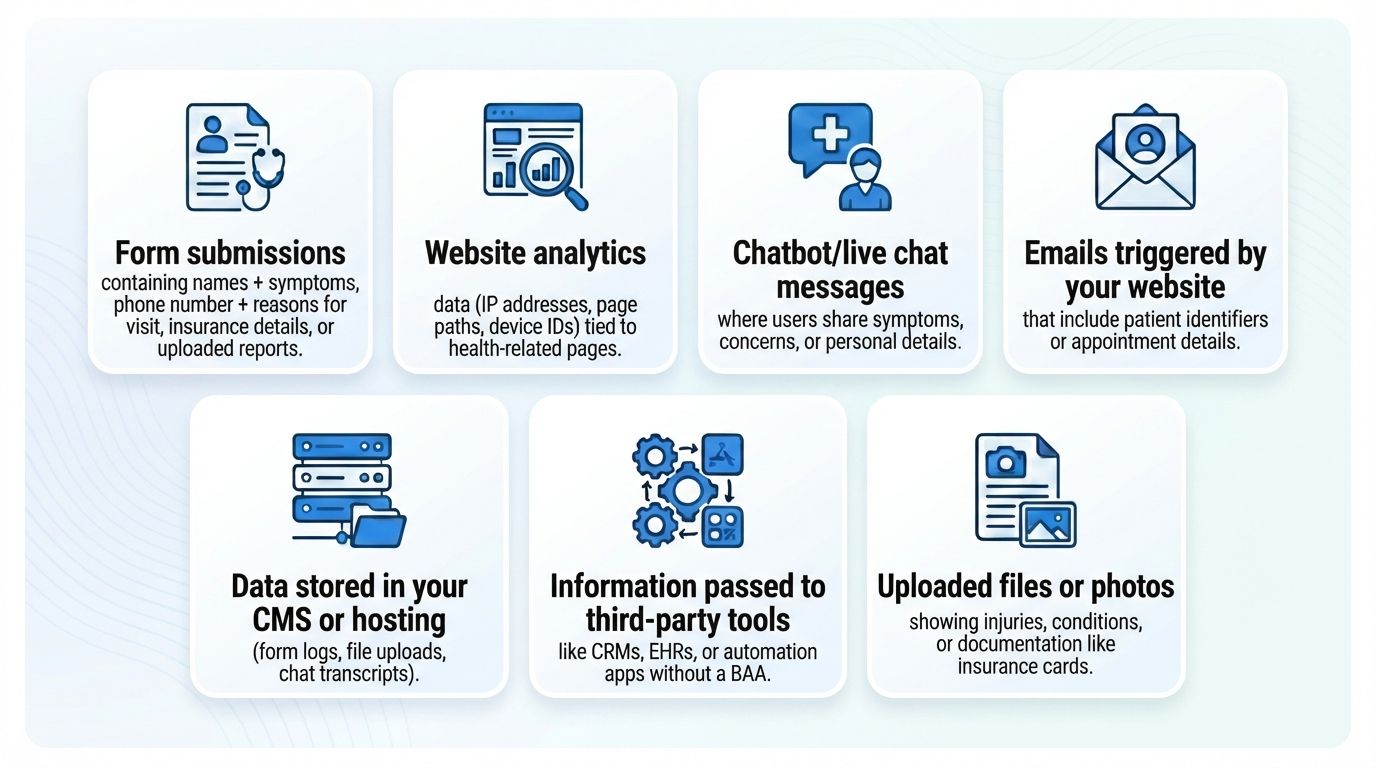
When it comes to websites, PHI is anything your site collects that can identify a patient and relates to their healthcare journey. Here are the PHI items that commonly appear on healthcare websites:
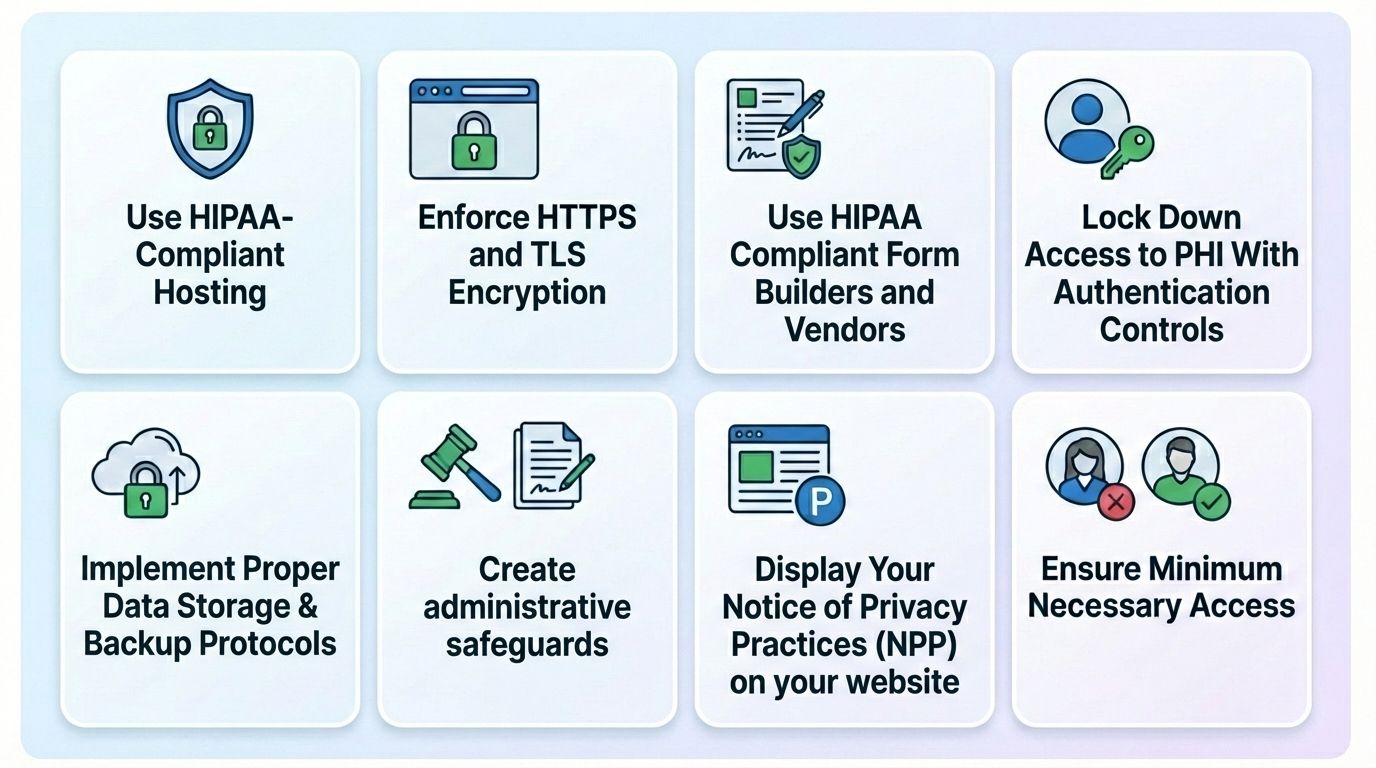
To stay HIPAA-compliant, every part of your website’s infrastructure must be secured. That means, your hosting, your third party apps, like form builders, analytics platforms, EHRs, all need to be HIPAA compliant.
Let’s get into the simple, most practical solutions for how you can achieve HIPAA compliance on your website, without breaking a sweat.
Your hosting provider must:
For this you need a hosting service that is HIPAA compliant, or HIPAA eligible. For example, AWS is HIPAA eligible. AWS signs a BAA and supports encryption, access controls, logging, and monitoring but Go Daddy does not. GoDaddy’s hosting on the other hand is not HIPAA compliant because the company does not sign Business Associate Agreements (BAAs).
Your entire website, especially patient-facing pages, must use:
Your hosting provider or website developer handles all three steps. Most HIPAA-compliant hosting platforms (AWS, Azure, etc.) provide built-in SSL installation options from their dashboards. HSTS is activated by your developer or your hosting/CDN provider by adding a security header (Strict-Transport-Security) to your website configuration. But many platforms like AWS, Cloudflare offer a simple toggle or setting to turn it on.
Pro tip: Enable automatic renewals for your SSL/ TLS encryption certificates to ensure there are no gaps in data security, and your website is always HIPAA compliant.
Any third-party tool touching your website’s PHI must:
This includes Form builders, Marketing CRMs, Chat widgets, Analytics tools (HIPAA-compliant alternatives), and SMS/email delivery tools
Let’s talk about form builders a little more in detail, because they are the most important category. It’s where PHI enters your system the most.
Professional online form builders like MakeForms, are 100% HIPAA compliant. They sign BAAs, offer encrypted submissions and US data residency, provide audit logs, and even have form templates available for HIPAA compliant intake forms, medical history forms, appointment forms, and more.
However, popular tools like Typeform, Wufoo, WixForms, do NOT offer HIPAA compliance or HIPAA compliant forms. If you are using any of these tools for your healthcare org or clinic, stop immediately. Because the HIPAA violation penalties are capable of putting you completely out of business.
When it comes to analytics tools, we would be remiss, if we do not mention that Google Analytics is also a hard NO for your healthcare website. This is one of the biggest hidden HIPAA violations. Tools like Google Analytics collect: IP addresses, Page visits tied to conditions, Device IDs, and if you have no BAA with them, you are collecting PHI improperly.
In fact, Google’s own documentation makes it clear: healthcare organizations should not use
Google Analytics on any page that contains or could reveal PHI, because Google does not sign a BAA for this product.
Only authorized staff should have access to PHI stored on your website or backend. The best way to do that is,
Role-based access: Create separate access for Admin, Clinician, Support, Billing, give each role only the permissions they need (least privilege). And enforce this inside your CMS, Form Builder, or auth system (AWS IAM) as well. HIPAA compliant form builders like MakeForms, already have role based access, and access logs to track who viewed/edited PHI built in.
Pro Tip: Maintain strong password policies (Force a mix of characters or use passphrases), and enable multi-factor authentication.
Following HIPAA’s Security Rule:
To achieve this, use storage systems that support built-in encryption (AES-256), examples: AWS RDS/S3 (with HIPAA), and turn on server-side encryption so data is automatically encrypted before being stored.
Set up automated daily backups, 7, 14, or 30 days, depending on your policy, and store these backups in a HIPAA-eligible storage bucket or snapshot vault. MakeForms, as HIPAA compliant form maker, also has automated backups for your data collected through forms.
HIPAA-compliant website, apart from technical guidelines like the above, also depends heavily on your internal administrative practices. This includes having a clear disaster recovery plan and ensuring your entire team is trained to follow HIPAA protocols during outages, breaches, or emergencies. Make these a part of your HIPAA practices:
Your website must provide clear disclosure of how patient data is collected, stored, and used. The best way to do this is to add a link to your privacy practices, which includes Information on patient rights (access, correction, revocation)
Finally, since everything is related to PHI handling, always remember to collect only the minimum required PHI. Which automatically means, you are storing and transmitting minimal PHI. Avoid unnecessary fields and remove sensitive data from emails.
For example, most clinics don’t actually need Social Security Numbers, full medical histories, or insurance details on initial website forms. Even appointment requests rarely require more than a name, contact information, and a brief reason for visit.
So reducing the amount of PHI = significantly HIPAA compliance risk = safer website.
This is where MakeForms becomes your simplest, most reliable solution for a HIPAA compliant website.
MakeForms is an online form builder for HIPAA compliant forms, designed specifically for healthcare organizations that need airtight security without sacrificing design or usability. Every form you create is encrypted end-to-end, stored in U.S.-based HIPAA-certified infrastructure, and fully protected under a signed BAA.
Whether you need HIPAA compliant online intake forms, HIPAA compliant web forms, HIPAA compliant website forms, or an entire suite of patient-facing HIPAA compliant online forms, MakeForms ensures your PHI enters your system safely — and stays secure at every touchpoint.
With built-in audit logs, role-based access, automated backups, and analytics controls, MakeForms is the easiest way to keep your website data collection compliant and modern at the same time.
If you want the fastest path to worry-free HIPAA compliance on your website, start with the tool that handles the most sensitive information: your forms.
Create a HIPAA compliant healthcare website form on MakeForm today.
If your website collects, stores, or transmits any PHI — through forms, chat widgets, analytics, or backend logs — then yes, the entire website must meet HIPAA requirements, not just the form pages.